Ahoy, crypto captains! The cryptocurrency seas glitter with promises of riches, but beneath the surface lurk cunning pirates ready to plunder your hard-earned funds. In 2025, hackers and scammers are more sophisticated than ever, weaving elaborate traps to exploit even the slightest misstep. Staying safe isn’t just smart—it’s your lifeline in this high-stakes world.
Here at The Whale Room, we turn every mistake into a lesson and every cautionary tale into a shield. Through the real-life stories of our crew, we’ll uncover 21 cryptocurrency scams that could drain your wallet dry. These tales aren’t just warnings—they’re your roadmap to outsmarting the scammers and securing your assets. Knowledge is power, and vigilance is survival. Let’s dive into the dangers and learn how to sail these waters safely.
Index
7. AI Deepfake Disaster: Liam Falls for a Fake Michael Saylor Video
9. Wallet Warning: Why Free Tokens Could Cost You Everything
10. Telegram Lurker Trap: Mia’s 2FA Mistake Drains Her Account
13. More Fake Kyle Incidents: Imposters Target the Whale Room
16. Discord Giveaway Trap: Dana’s Wallet Drained by a Promise
18. Telegram Trading Scam: Finn’s 0.3 BTC Vanishes in a Flash
21. No-2FA Blunder: Riley’s Phishing Fumble Costs Him Everything
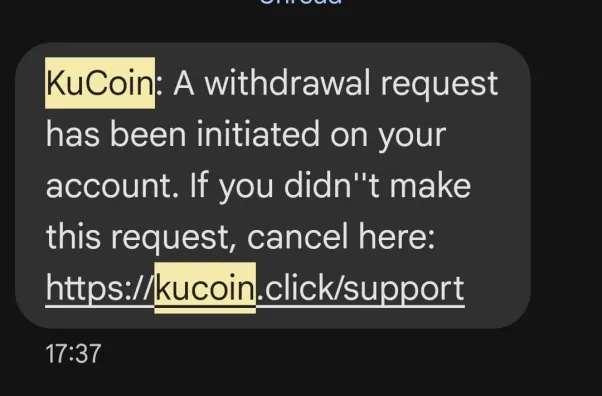
1. Fake SMS Scam: How Dane Lost His KuCoin Funds in Minutes
Dane, a seasoned trader in The Whale Room, thought he’d seen every trick in the book—phishing emails, fake websites, you name it. But one morning, a cunning SMS scam nearly sank him.
While sipping his coffee, Dane received this text:
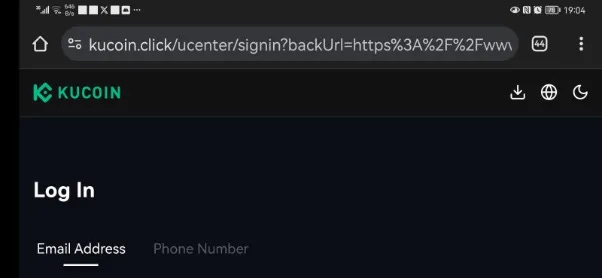
Panic surged through him. He wasn’t trading, so this seemed real. Clicking the link, he landed on a page mimicking KuCoin’s support site, complete with branding and a login prompt:
Dane entered his credentials, thinking he was thwarting a theft. Instead, he handed scammers the keys to his account.
The SMS wasn’t from KuCoin—it came from a .click domain, not kucoin.com. Using a SIM swap attack, scammers hijacked his phone number, bypassing SMS-based 2FA. Within minutes, they drained his funds into anonymous wallets. Dane only realized the truth when a legitimate KuCoin email confirmed the withdrawals—too late.
Tip: Always verify URLs against official sources, like KuCoin’s X.com page (check follower count for legitimacy). Never click SMS links blindly.
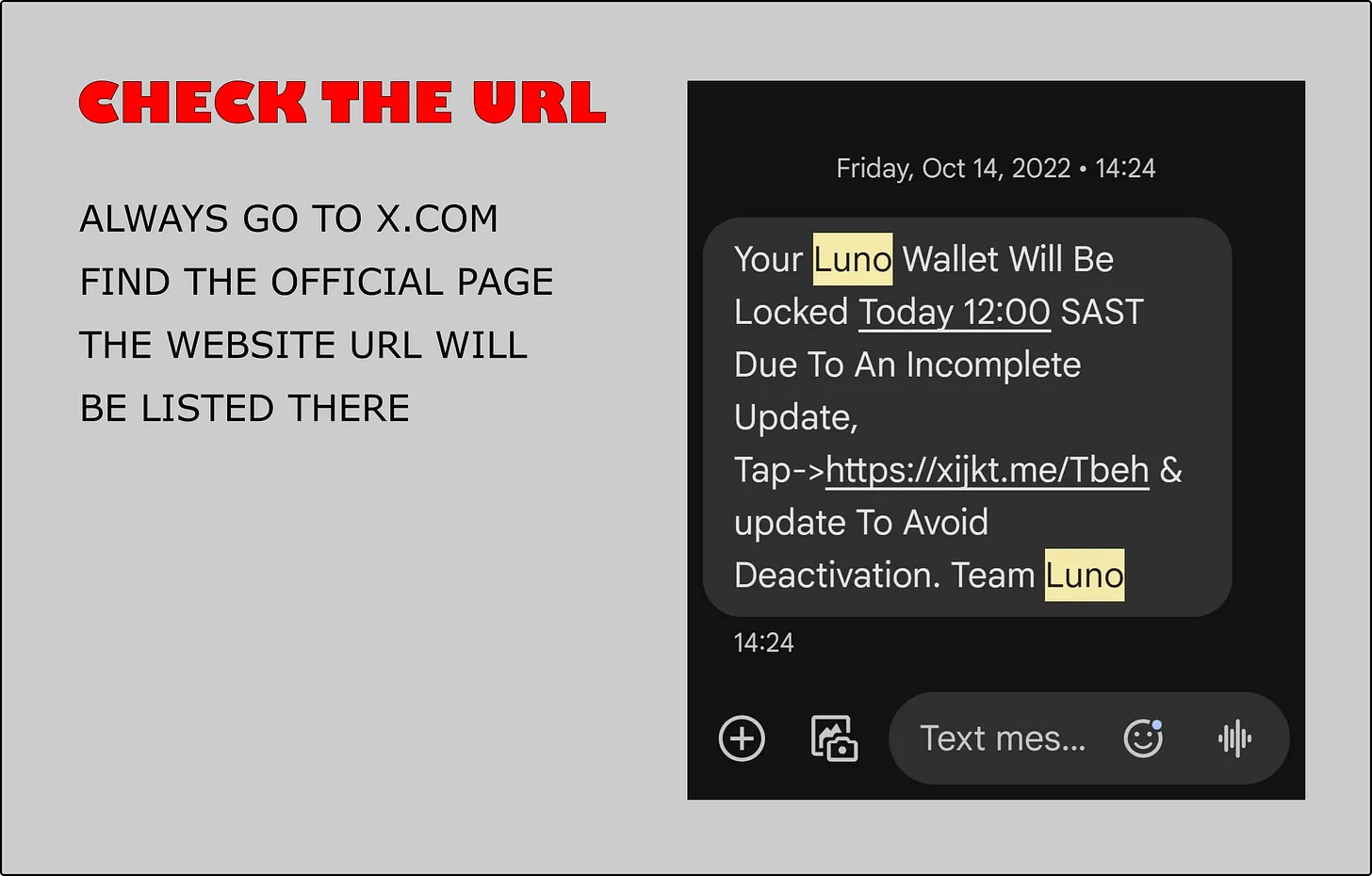
2. Master URLs to Spot Fake Crypto Websites Like a Pro
Spotting fake URLs is a crypto survival skill. A great resource explains it clearly:
https://www.aura.com/learn/how-to-identify-fake-websites
Educate yourself—once you grasp domains, spotting scams becomes second nature.
3. Phishing Email Trap: Tom’s $50,000 Lesson in Vigilance
Captain Tom kept $50,000 in his exchange account. One morning, he received an email with the subject line: "Action Required: Update Your Account to Avoid Lockout." The email appeared legitimate, complete with official branding and a link to "secure" his account.
Thinking it was urgent, clicked the link and followed the instructions.
The webpage looked identical to his exchange’s login page.
Username? Password? Done. He even double-checked that his credentials were updated correctly. Feeling accomplished, he logged off and took his trusty pup for a walk.
What he didn’t know was that the link directed him to a fake phishing clone controlled by hackers. Hackers snatched his credentials and emptied his account.
Tom only noticed when a $50,000 withdrawal hit his phone mid-stroll.
Tip: Hover over links before clicking—legit emails won’t redirect to odd domains.
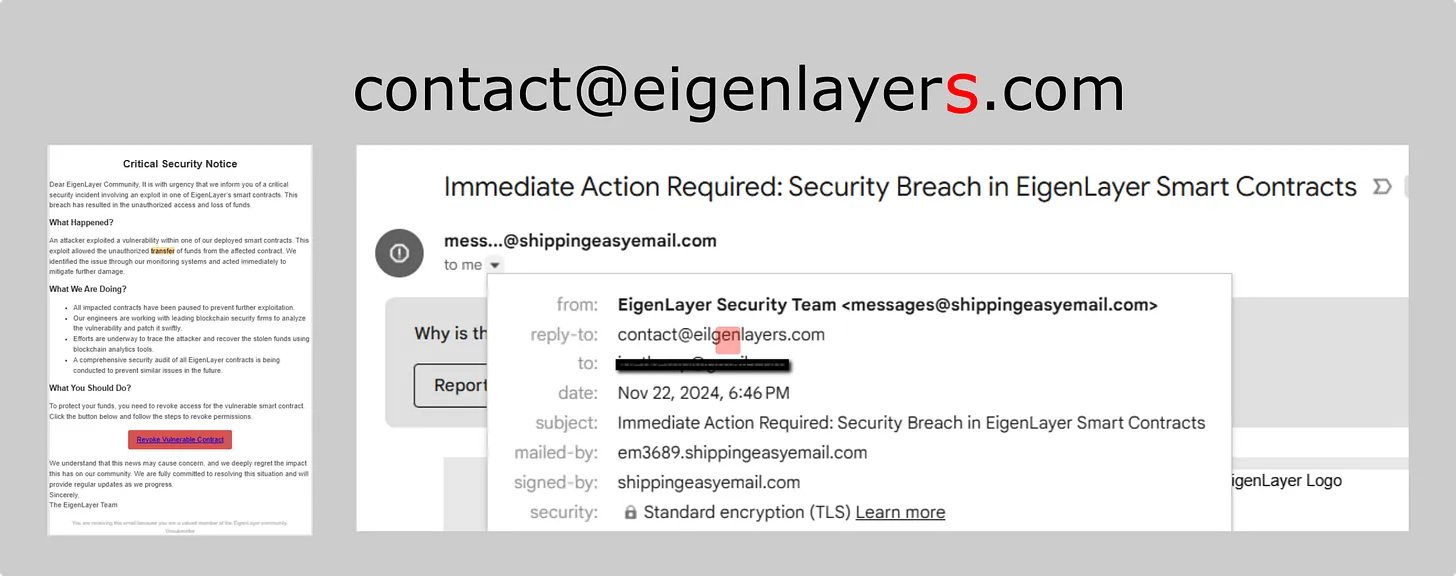
4. Similar Email Scams: Spotting the Subtle Signs of Fraud
5. More About Email Scams
Scammers often mimic legit emails with subtle flaws—like typos in domains (e.g., "contact@eigenlayer.com" vs. "contact@eigenlayers.com").
6. Public Wi-Fi Nightmare: Sarah’s $10,000 Crypto Theft
Sarah was eager to check her portfolio while sipping coffee at her favourite café.
The café’s free public Wi-Fi offered an easy way to connect, and without much thought, Sarah clicked "connect" and launched her browser. Shortly after, she opened an email with the subject line: "Unusual Account Activity Detected – Verify Immediately." The message appeared urgent and professional, with her exchange’s logo at the top and a link to log in and review her account.
Her pulse quickened. Could someone have attempted to access her funds? The email read: "To protect your account, please confirm your credentials immediately." She felt a mix of anxiety and responsibility, thinking, "Better safe than sorry." She clicked the link and was taken to a page that looked exactly like her exchange’s login portal.
She typed her username. Password? Done. Once she logged in, she was relieved to see her balance untouched, and there were no signs of suspicious activity. Reassured, she closed the browser and took another sip of her coffee.
What Sarah didn’t know was that the email she had received wasn’t from her exchange at all—it was from a hacker. The link had directed her to a phishing site, an identical replica of her exchange’s login page. Every keystroke she entered was sent directly to the hacker in real time.
Worse still, the café’s public Wi-Fi was compromised. The hacker, connected to the same network, used a “man-in-the-middle” attack to monitor data being transmitted. They intercepted her credentials as she typed them.
Just as she started packing up to leave, her phone buzzed. A notification: "$10,000 withdrawal completed." Confused, she reopened her exchange app only to see a second transaction processing. By the time she managed to freeze her account, her funds had been siphoned off into untraceable wallets.
Sarah learned a hard lesson that day. Public Wi-Fi, no matter how convenient, is dangerous terrain for crypto traders.
Tip: Use a VPN to encrypt your connection on public networks.
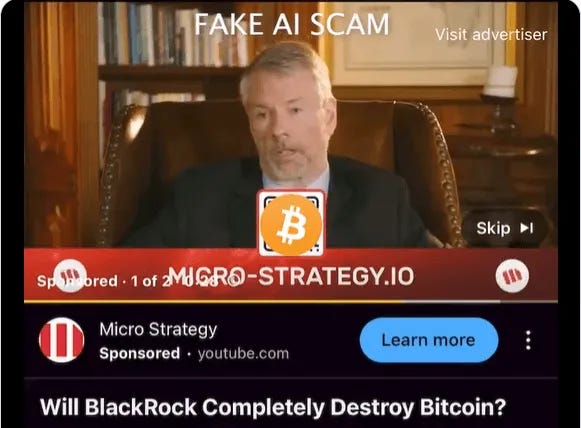
7. AI Deepfake Disaster: Liam Falls for a Fake Michael Saylor Video
Liam, a Bitcoin enthusiast, stumbled on a YouTube “live stream” titled: “MICROSTRATEGY EVENT: Michael Saylor Announces Bitcoin Bonus Giveaway!” Saylor promised to double BTC sent to a wallet address:
“To celebrate Bitcoin reaching new milestones, MicroStrategy is doubling Bitcoin investments! Send any amount of BTC to our official address, and we’ll send back double the amount as a thank-you to the crypto community.”
Comments raved: “Sent 0.5 BTC, got 1 BTC back!” Liam sent 0.1 BTC. Hours later, the video vanished—revealing an AI deepfake scam.
Seeing the overwhelming “proof” in the comments and with the clock ticking, Liam decided to take a chance. He scanned the QR code and sent 0.1 BTC to the address. Feeling confident, he waited for the doubled return to arrive.
Minutes turned into hours, and no Bitcoin came back. Suspicious, Liam tried to revisit the video, but it had been taken down. Realization dawned on him: he had been scammed. The video wasn’t an official MicroStrategy production—it was an AI-generated deepfake designed to mimic Michael Saylor.
Tip: Verify giveaways through official X posts, not YouTube hype.
8. Malware Mayhem: Jake’s Wallet Keys Stolen by a PDF
Jake prided himself on being tech-savvy, often scouring the web for market insights and crypto strategies to stay ahead of the curve.
One day, an email landed in his inbox with the subject line: "Exclusive Report: Bitcoin’s Next Big Move Revealed!" The sender appeared to be from a well-known crypto analytics platform that Jake frequently follows. He opened an email attachment: "CryptoTrends2024.pdf." Nothing loaded, so he moved on.
Silently, malware began working in the background, scanning his computer for sensitive data. It didn’t take long for the program to locate a file on Jake’s desktop labelled "My Wallet Keys.docx."
Within minutes, Jake’s funds were being siphoned off to untraceable addresses. A few hours later, Jake opened his wallet to check on a recent deposit, only to find his balance at zero.
Tip: Scan attachments with antivirus software before opening..
9. Wallet Warning: Why Free Tokens Could Cost You Everything
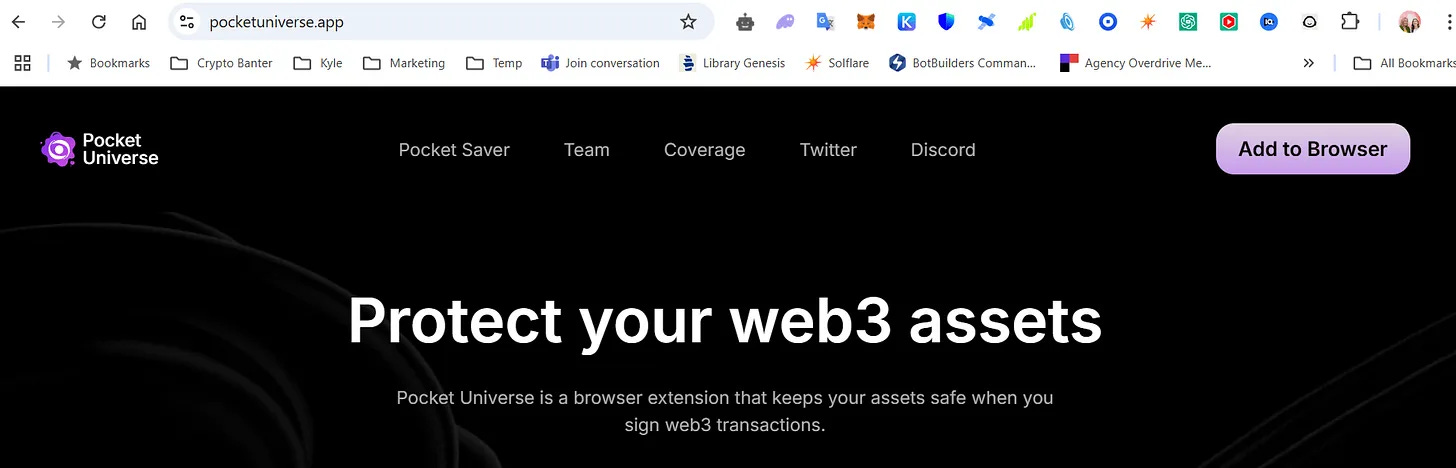
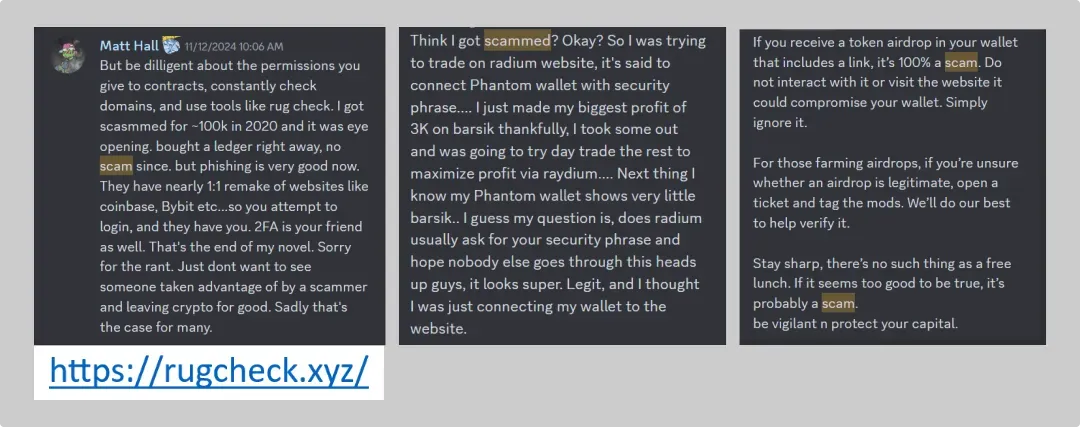
Beware unsolicited “free tokens” in your wallet—they’re often bait for scams. Use tools like Pocket Universe to vet links.
https://www.pocketuniverse.app/ is an extension that you can add to your browser. When you click through your wallet to a link it will warn you when a website is a possible scam. They even offer insurance in case you got scammed.
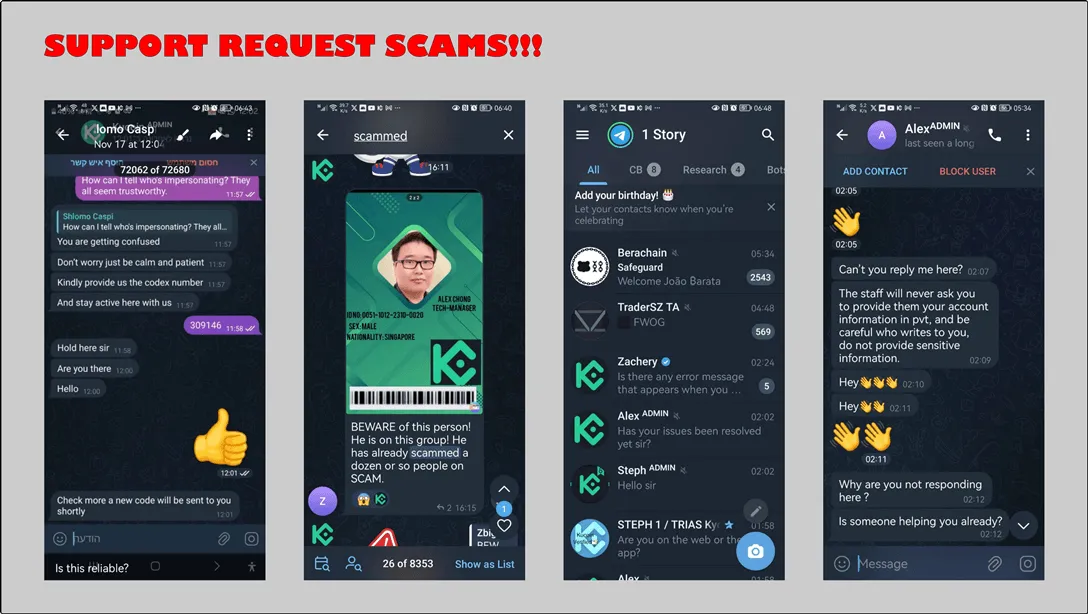
10. Telegram Lurker Trap: Mia’s 2FA Mistake Drains Her Account
Mia posted in KuCoin’s Telegram group about login issues. A “KuCoin_AdminSupport” DM’d her, requesting her 2FA code. She complied—minutes later, her account was drained.
The urgency in the tone and the promise of quick resolution made Mia hesitate, but the “admin” pressed on:
"Mia, if we don’t resolve this now, your account could remain at risk. Please send the 2FA code immediately so we can secure your funds."
Feeling the pressure, Mia complied and shared the code. Within minutes, she received notifications of unauthorized KuCoin withdrawals.
I personally tested this. I went on the KuCoin chat on Telegram and pretended I couldn’t login into my KuCoin account. A minute later I had 4 so-called admins offering support.
Do not reply to ANY Telegram private support. The moment someone comment and tell you to DM him because he can help, RUN!
In one of my recent blog posts, a reader asked me advice about how to register on an exchange. And soon he received a reply from a reader. “I’m here to help you Todd, I just sent you a message”
Even if it is from a person with the best intentions, you will never know if it is a scammer.
DO NOT respond to messages like these. If you need help, ask on a trusted platform such as our Whale Room and expect a reply on that same server. The moment you receive a private message offering help…well you know now what to do, right?
Tip: Never share 2FA codes. Not even to ‘support’ personnel. Legit support won’t DM you but will publicly give advice. Exchanges typically have a process via email to resolve issues.
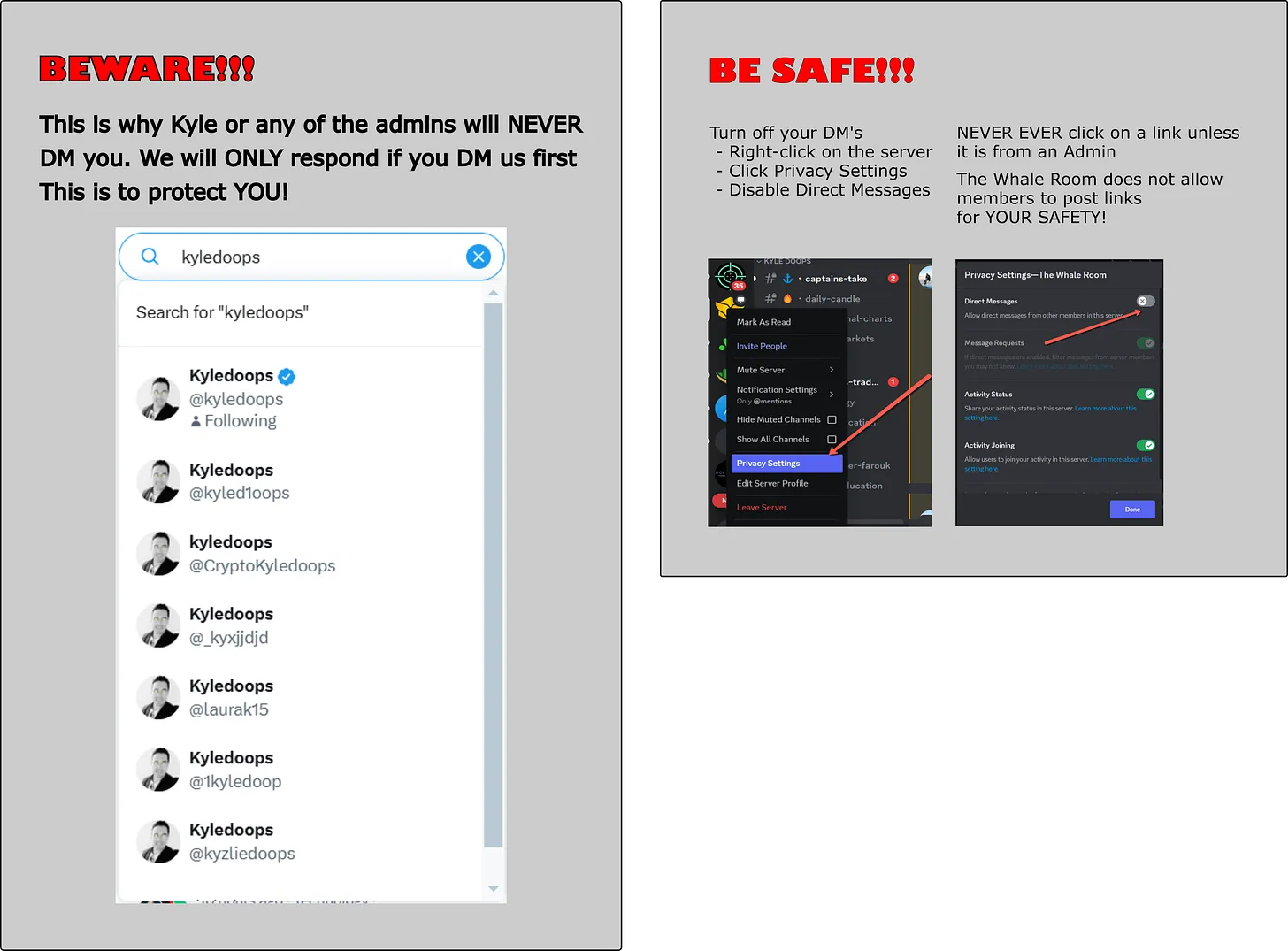
Block your DM’s on Discord!
11. Password Reuse Peril: Leo’s Simple Habit, Massive Loss
Leo reused passwords across exchanges. A minor breach exposed one. Using the stolen information, they ran Leo’s email and password combination through other major exchanges. To their delight, the hackers discovered that Leo used the exact same credentials on several platforms and drained thousands in minutes.
Tip: Use unique passwords for every exchange and use a password manager.
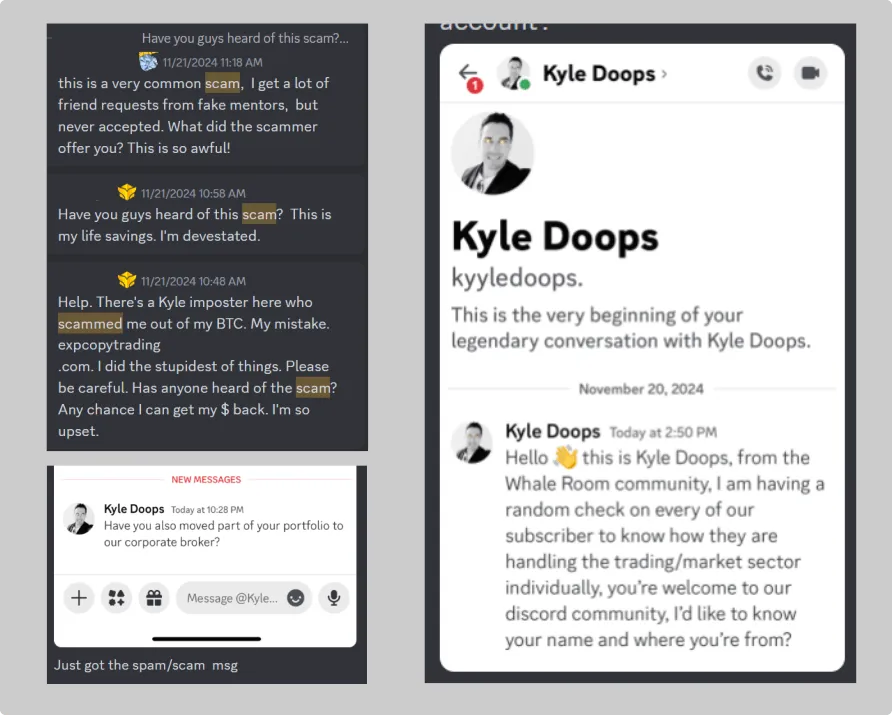
12. Fake Captain DM: Eric Scammed by a Trusted Face
Eric got a DM from “Kyle,” The Whale Room’s captain, offering to trade for him. Flattered, he sent 0.5 BTC. It was a scammer using Kyle’s photo.
Tip: Verify identities in trusted group chats, not DMs.
Never think it can’t happen to you—scammers thrive on overconfidence. Together, the Whale Room navigate safely, sharing knowledge and staying one step ahead of those who lurk in the shadows. Join us and let’s sail securely toward success. 🌊 Sign Up Here
13. More Fake Kyle Incidents: Imposters Target the Whale Room
Scammers mimic trusted figures—always double-check.
14. SIM Swap Heist: Maya’s Phone Number Became Her Downfall
One afternoon, Maya’s phone suddenly lost service—no calls, no texts, no data. She assumed it was a minor issue and decided to troubleshoot later. What she didn’t know was that hackers had executed a SIM swap, convincing her mobile provider to issue them a new SIM card tied to her number.
With control of her phone number, the hackers reset her exchange account passwords, bypassing SMS-based 2FA. Within minutes, they gained access to her accounts, drained her wallets, and sent her funds to anonymous addresses.
Tip: Switch to app-based 2FA (e.g., Google Authenticator).
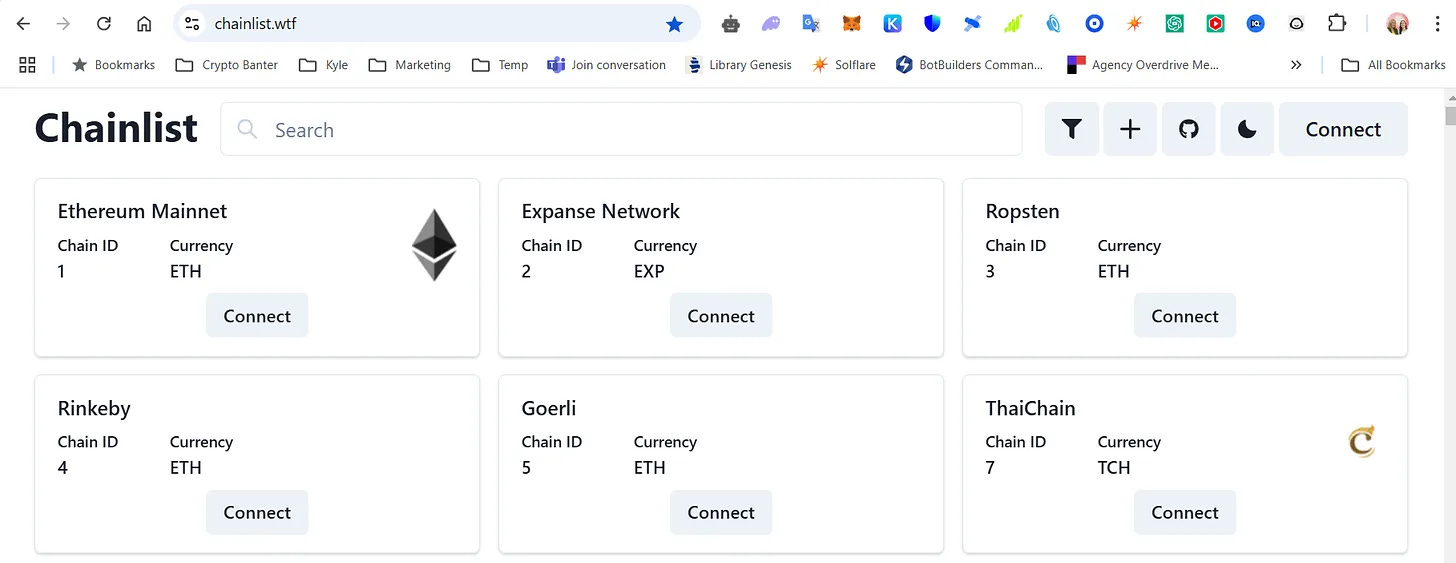
15. Chainlist Imposter: Jules Loses Funds to a Fake Site
One day, while setting up a new project, Jules needed to add a blockchain network to his MetaMask wallet. Knowing that Chainlist.org was the go-to platform for such tasks, he quickly Googled "Chainlist" to find the link.
The top result wasn’t Chainlist.org but a similar-looking site with a different extension
At first glance, it didn’t look exactly like the original, but it seemed professional enough. Jules thought, “This must be the right one—it’s at the top of Google’s search results.”
Jules connect his wallet to add the network automatically. He approved the connection request in MetaMask. But what Jules didn’t realize was that this was a scam site. Instead of adding a legitimate network, it added a malicious smart contract with hidden permissions to transfer funds.
Later, Jules learned from The Whale Room that the real Chainlist.org provides its official link through trusted channels, like their verified X.com (formerly Twitter) account. Had he double-checked the link there, he could have avoided the fake site.
Tip: Bookmark legit sites or check X for official links.
16. Discord Giveaway Trap: Dana’s Wallet Drained by a Promise
Dana joined a new Discord server to participate in a project she had been excited about. Dana eagerly explored the various channels. Among them was a “Verify Humanity” channel, a common feature in crypto Discords, where users usually complete simple steps to access the rest of the server.
What Dana didn’t know was that the server admins weren’t vigilant about managing permissions. A scammer had managed to post a link in the channel, cleverly disguised as part of an official giveaway event. The message read:
“Congratulations! To celebrate our project launch, today we’re giving away free rewards to verified users. Claim your bonus here: [maliciouslink.xyz].”
Dana, excited at the thought of being part of the project’s early supporters, hurried to connect her wallet.
As soon as she approved the connection, the scam site executed a malicious contract. Funds began disappearing from Dana’s wallet almost instantly.
Dana later discovered that the admins had allowed open posting permissions, enabling bad actors to exploit the channel and deceive users.
Tip: Avoid wallet connections unless verified.
17. Free Airdrop Lies: The Hidden Dangers of Crypto Rewards
“Free airdrops” asking for wallet connections are traps.
18. Telegram Trading Scam: Finn’s 0.3 BTC Vanishes in a Flash
Finn, a budding trader and loyal member of The Whale Room joined a Telegram group that promised the best trading signals in crypto.
Initially, Finn followed some of the free trading calls. While his results were underwhelming, the group’s updates always highlighted massive wins. Each screenshot they posted showed incredible profits, accompanied by comments like: “Premium members are making bank today!” Feeling like he was missing out, Finn decided to dive deeper.
The admins soon rolled out an exclusive opportunity:
“Why stress over trades? Let us handle everything for you. With our expertise, you’ll see 3–5x growth in just a month! Sign up on our platform and let us take care of the rest.”
Finn deposited 0.3 BTC onto their platform, excited to let the “experts” grow his funds.
After the deposit, Finn’s account still showed a 0 balance on the website.
When Finn tried to cancel his subscription and requested a refund, he encountered the first hurdle. His refund request was met with vague messages, and support responded with excuses about “market delays” and “technical issues.”
Upon closer inspection of the website, several glaring red flags became obvious. There was no link to any terms and conditions, a critical omission for any legitimate financial platform. The About Us page was riddled with stock photos of smiling “team members” that could be found with a reverse image search. The website also lacked genuine testimonials—just vague claims of success without any identifiable user stories.
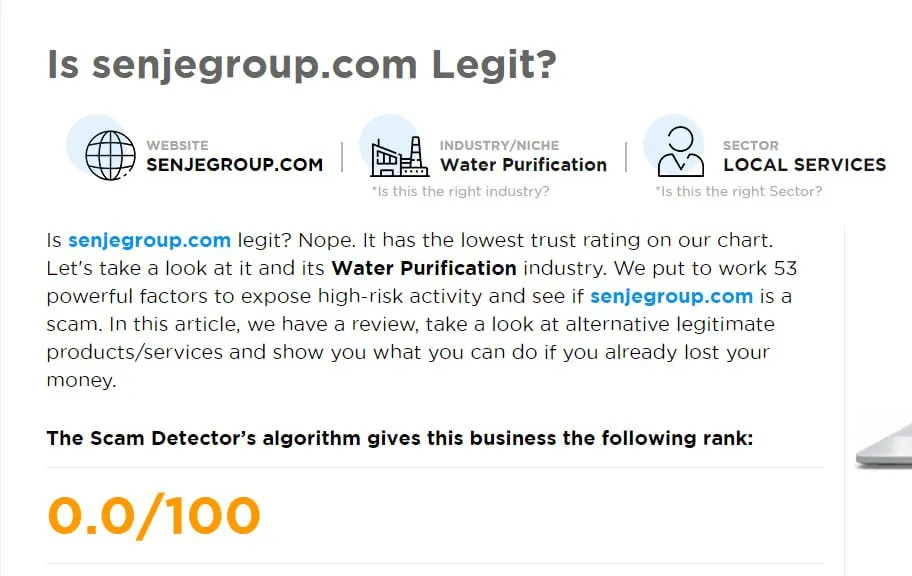
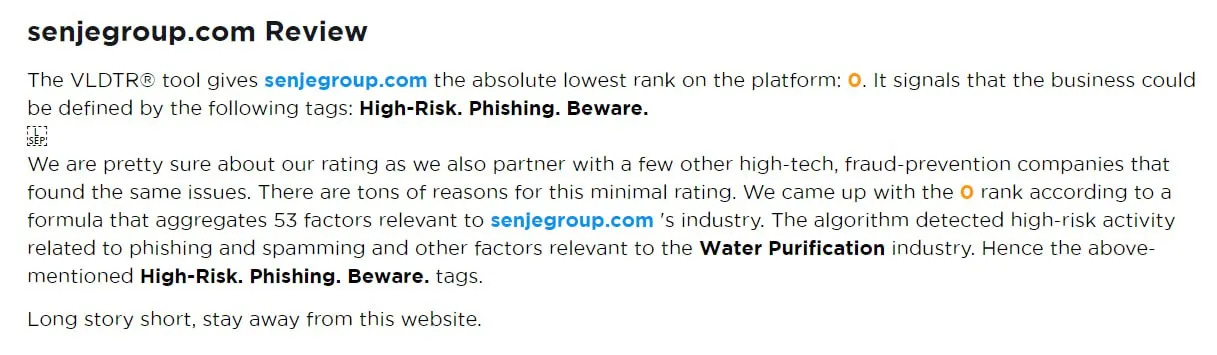
Even more troubling was the fact that the admins marketed themselves as financial advisors, but their credentials were nowhere to be found. A quick online search revealed scam warnings from other traders who had fallen into the same trap. In fact the same URL was previously used to promote water purification services.
Finn had ignored several subtle but critical warning signs, dazzled by the allure of quick profits. The Telegram group, the flashy website, and the constant updates were all part of an elaborate ruse designed to lure traders into depositing funds that they’d never see again.
19. Café Camera Capture: Alex’s Screen Exposed His Crypto
Alex often worked from his favorite café. On one such day, Alex logged into his exchange account to check on an open trade. He typed his username and password quickly, his focus entirely on the market charts displayed on his laptop.
What Alex didn’t notice was a small camera discreetly mounted behind him, angled perfectly to capture his laptop screen. A hacker in the café had set up the camera to record unsuspecting patrons as they entered sensitive information like passwords.
The hacker logged into his exchange account and initiated withdrawals. Since Alex hadn’t enabled two-factor authentication, there was nothing to stop the hacker from draining his funds.
Tip: Shield your screen in public.
20. Public Wi-Fi Spyware: Ella’s Trade Turns Into a Theft
One day, while attending a co-working space, Ella noticed a sudden market movement and decided to make a quick trade.
Spyware nabbed her credentials and drained her account. The hacker, lurking on the same network, monitored Ella’s activity in real-time. By intercepting her connection, the hacker captured her login credentials, including her username and password.
Tip: Use a VPN—NordVPN comes highly recommended. Get it here.
21. No-2FA Blunder: Riley’s Phishing Fumble Costs Him Everything
Riley, always followed market updates and kept his portfolio diversified, but his focus on trading meant he overlooked one critical detail: setting up two-factor authentication (2FA) on his accounts.
One day, Riley received an email with the subject line: “Urgent: Suspicious Login Detected.” The message appeared to be from his exchange. The email urged him to “verify his credentials immediately” to secure his funds.
Riley clicked the link, which led him to a page identical to his exchange’s login portal. However, this link had directed Riley to a fake website that captured his credentials in real time. The hackers quickly logged into his real account, bypassing security since Riley hadn’t set up 2FA.
Tip: Enable 2FA on every account.
🐋 Swim with the Whales
In The Whale Room, our traders thrive:
Christo Columbus: 114% gain on $XRP.
Farouk: 28% on $RUNE, 214% on $WIF.
Let us continue to celebrate the remarkable achievements of our traders and community. Here's to navigating the crypto seas with precision and confidence. Look at what our members achieved recently.
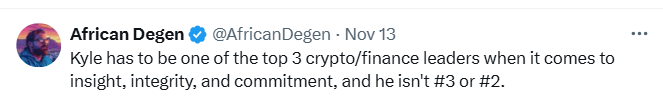
Captain Kyle leads with integrity.
Conclusion: Security is Survival
These 22 scams prove one thing: small mistakes can cost you everything. Stay sharp—join The Whale Room to navigate safely. Sign Up Here.
Tell me below: Have you been scammed? Share your story—I read every comment!
Help Spread the Word!
If you’d like to help me spread the word, all you have to do is send one friend a personal email where you tell them all about today’s blog.
Chat soon!
Inet Kemp